· 11/14/2024 ·
Intel® Transparent Supply Chain (TSC)
The Intel Transparent Supply Chain (TSC) comprises policies and procedures that OEMs/ODMs use while manufacturing their products. This process occurs before the products are shipped. The OEMs use the information collected to ensure transparency in their manufacturing process. IT departments use the information produced by the TSC to validate their platforms. TSC helps provide an ecosystem of trusted providers from transparent manufacturing processes that IT departments can rely on for products.
Transparent supply chain overview
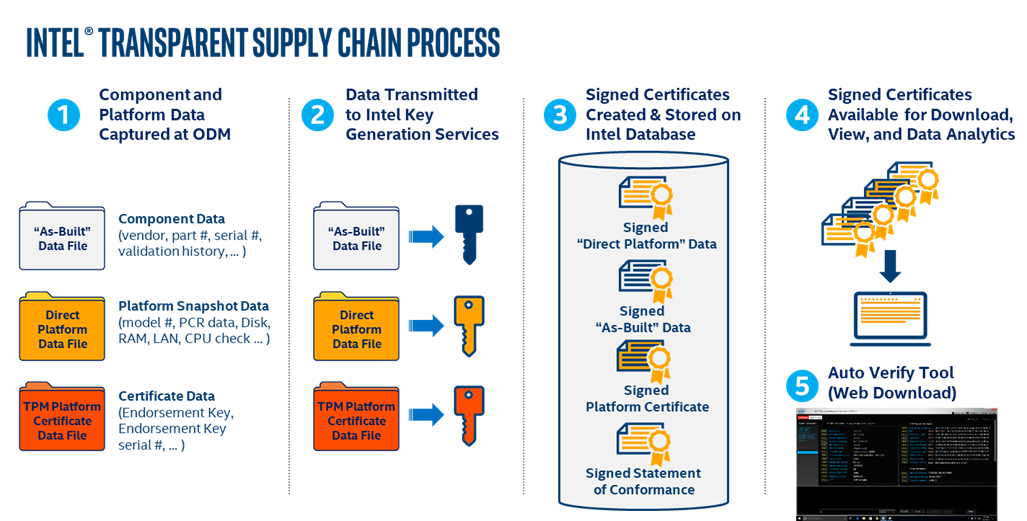
The Intel TSC is composed of five separate processes:
- Component and Platform data is collected in real-time at the ODM Factory using tools that read the platform information during manufacturing.
- Data collected at the ODM is securely transmitted to Intel using Secure File Transfer Protocol (SFTP).
- Once Intel receives the data collected during the manufacturing process, the data is signed by Intel at Intel’s High-Security signing facility using Intel’s Signing Certificate Authority.
- The signed data files are then uploaded to the TSC database for storage and retrieval by the web portal.
- The TSC web portal enables the user to download the Auto Verify Tool and the signed platform data files.
Intel® transparent supply chain web portal
The Intel® TSC Web Portal provides access to the Intel TSC data files for Intel TSC-enabled systems. The Intel TSC Web Portal enables admin users to manage Admin API keys and users. The Web Portal also contains documentation and down load links for The Intel Auto Verify Tool and the Verify Utility. The user also has the option to remove their account and personal information from the web portal in compliance with GDPR.
The TSC Verify Tool can be downloaded from the Web Portal once access has been granted.
The TSC Web Portal is located on the Intel® TSC domain URL: https://portal.tsc.trustauthority.intel.com/
TSC verify tool overview
The TSC Verify tool is a standalone application that runs under the Windows operating system. The tool performs many functions:
- Scanning the system component information.
- Writing the Platform Components out to a Direct Platform Data (DPD) file
- Validation of the Platform Certificate issued to the platform.
- Validation of the Direct Platform Component file generated at the factory during manufacturing.
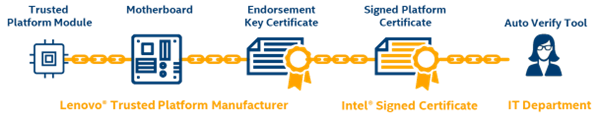
X.509 platform certificates
Every platform has a unique X.509 Platform Certificate signed by the Intel Signing Authority. This unique Platform Certificate is cryptographically bound to the system through the TPM module installed during manufacturing.
Platform certificates validation
- Verifies that the platform TPM module matches the signed platform certificates.
- Platform Attestation is confirmed by comparing the TPM module's Endorsement Key Serial Number against the System Serial Number and Motherboard Serial numbers.
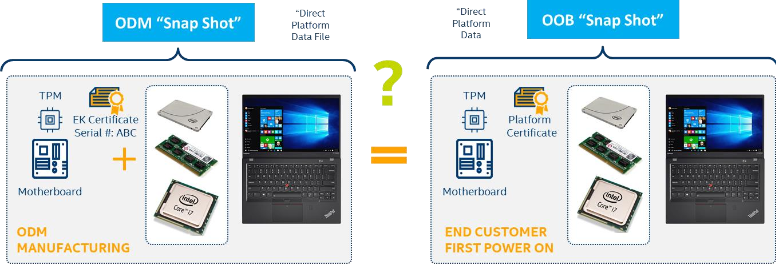
Direct platform data snapshots
The Intel TSC Verify Tool generates direct platform data snapshots. These snapshots scan the platform and generate direct platform data. The updated snapshots are used when there are changes in the platform.
Direct platform components validation
The direct platform components validation compares the snapshot of the platform component data taken during manufacturing with the snapshot taken at the first boot. It answers the question: "Is the platform that arrived at the customer the same as the one that shipped from the ODM's factory?" Any changes in the Direct Platform Data from the ODM to the Customer is flagged.
TSC verify tool download and installation
TSC verify tool system requirements
The Windows version of the TSC Verify Tool is compatible with Windows 10, WinPE, and Windows Server 2016/2020. The tool is provided as a signed executable file named TSCVerifyTool.exe.
TSC verify tool download
The TSC Verify Tool zip file is downloaded from the Intel TSC Web Portal.
Log in to the Intel TSC web portal.
Download the TSC verify tool zip file.
Create the following directory:
`C:\TSCVERIFY
Move the TSC verify tool zip file to the directory.
Extract the contents of the TSC verify zip file into the TSCVERIFY directory.
The TSC verify tool zip contains 2 files:
TSCVerifyTool.exeThe TSC Verify Tool Windows User Manual- this document.
Open a command prompt.
Navigate to the folder in which the
TSCVerifyTool.exewas extracted.Run the following command to execute the TSC the TSC verify tool.
C:\Users\TSCVERIFY\TSCVerifyTool.exe
TSC Verify Tool System Requirements
The Windows version of the TSC Verify Tool will run on Windows Operating Systems
such as Windows 10 or higher, WinPE, and Server 2016 / 2020. The TSC Verify Utility is distributed in a signed executable: TSCVerifyTool.exe
TSC Verify Tool commands
The TSC Verify Utility is a command-line executable that runs in the Windows Command Prompt.
The TSC Verify Utility has the following commands:
SCANSYSTEM - This command scans the platform to read the current platform values and outputs the platform component values to the console. No input or output file is associated with the SCANSYSTEM command; the output is directed to the console.
READFILE - This command reads the Direct Platform Data file specified by the –in option and outputs the values to the console. Only one input file is allowed for this command.
SCANREADCOMP - This command scans the platform to read its current values. It then reads the Direct Platform Data file specified by the –in option and compares the values. The comparison results are output to the console. If the –fl flag is included, the results are also written to the specified output file..
PFORMCRTCOMP - This command compares the contents of the signed platform attribute certificate file specified by the –in option to the current information from the system. It detects changes in elements like the EK Serial Number from the Trusted Platform Module and the Platform Serial Number in the system. It also compares the platform configuration from the file against the current components of the system. The results of the comparison are sent to the console. The command indicates whether changes were detected at the system or component level as yellow warning messages.
If the result of the comparison is successful, then a success message is displayed saying PFORMCRTCOMP PASS.
If the result of the comparison is not successful, then it displays PFORMCRTCOMP FAIL. It also shows the differences line by line in red.
WRITEDELTAFILE - command allows to generate new delta xml file that will include only the platform components that have been either added, modified or removed from the original system setup. It will perform a comparison of all the platform components based on current platform information and taking as input the base platform attribute certificate file and optionally passing a list of previous delta attribute certificates files.
CASIGVERIFY - This command verifies the signature of the TSC Issuing CA file. Optionally, it also verifies the signature of a signed platform attribute certificate or Direct Platform Data File using the public key of the TSC Issuing CA certificate.
The TSC Issuing CA file is specified by the –ca option. The signed platform attribute certificate or signed Direct Platform Data File is specified by the –in option. The CASIGVERIFY command will only verify one file at a time.
The following is the Command Line Syntax of commands and options:
READFILE
| Tool | Command | Options | Description |
|---|---|---|---|
| TSCVerifyTool | READFILE |
-in, /in |
Flag allows user to read from input file. |
-ca, /ca |
Flag allows user to load CA cert. |
SCANREADCOMP
| Tool | Command | Options | Description |
|---|---|---|---|
| TSCVerifyTool | SCANREADCOMP |
-in, /in |
Flag allows user to read from input file. |
-ca, /ca |
Flag allows user to load CA cert. | ||
-fl, /fl |
Flag allows user to write output file. If the file exists, then it will be overwritten, otherwise, it will be created. |
SCANREADCOMP
| Tool | Command | Options | Description |
|---|---|---|---|
| TSCVerifyTool | PFORMCRTCOMP |
-in, /in |
Flag allows user to read from input file. |
-ca, /ca |
Flag allows user to load CA cert. | ||
-d, /d |
Flag allows user to specify a list of delta input files. All files must exist. |
CASIGVERIFY
| Tool | Command | Options | Description |
|---|---|---|---|
| TSCVerifyTool | CASIGVERIFY |
-ca, /ca |
Flag allows user to load CA cert. |
-in, /in |
Flag allows user to read from input signed file. |
WRITEDELTAFILE
| Tool | Command | Options | Description |
|---|---|---|---|
| TSCVerifyTool | WRITEDELTAFILE |
-in, /in |
Flag allows user to read from input file. |
-ca, /ca |
Flag allows user to load CA cert. | ||
-d, /d |
Flag allows user to specify a list of delta input files. All files must exist. | ||
Miscellaneous options
The flags listed below can be used with any of the commands listed in the above tables.
| Tool | Command | Options | Description |
|---|---|---|---|
| TSCVerifyTool | -vl, /vl |
Flag to turn on verbose messages. | |
-notpm, /notpm |
Flag to allow user to collect DPD on non-TPM system or board. | ||
-nohdd, /nohdd |
Flag to allow user to skip the hard drive in generating DPD file. | ||
-noamt, /noamt |
Flag to skip the Intel® AMT bit verification. | ||
-ecc, /ecc |
Flag to specify to retrieve the EK TPM certificate using ECC algorithm. | ||
-server, /server |
Flag to support server features: BMC, FRU, SDR & etc. | ||
-dsg, /dsg |
Flag to support DSG server configurations. |
Utility tool status return value
The TSC Verify Utility returns an integer value for pass and fail: Return values.
- 0 – PASS
- 1 – FAIL
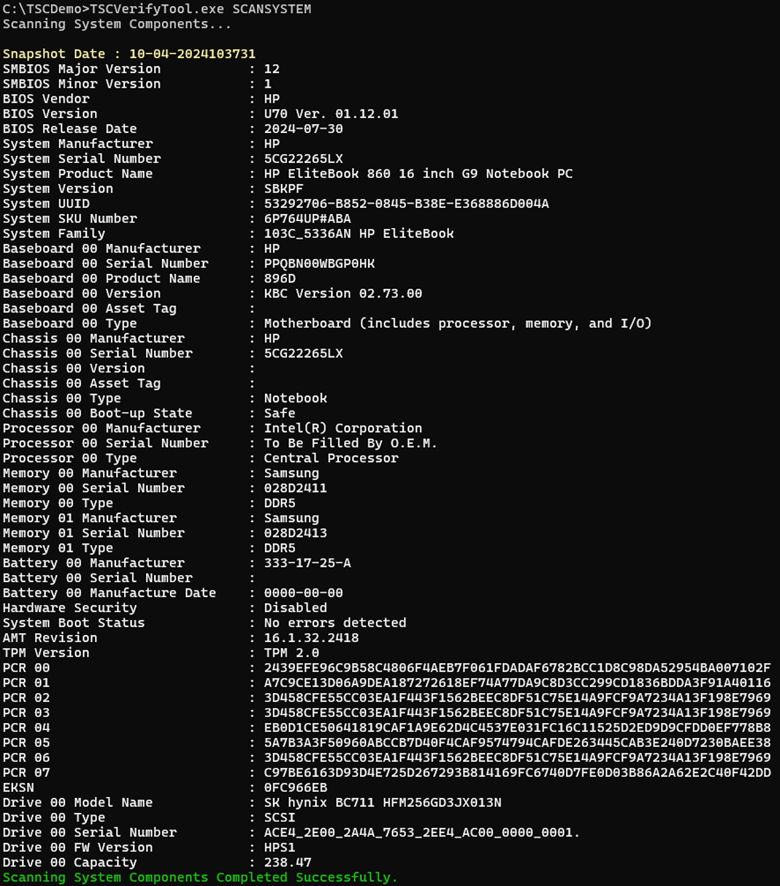
Scan system command SCANSYSTEM
This command scans the platform to read the current platform values and sends the platform component values to the console. The SCANSYSTEM command does not involve an input or output file; all output is directed to the console.
The SCANSYSTEMcommand performs the following operations:
- Reads the System BIOS DMI Tables for BIOS, system, motherboard, chassis, processor, memory, security/AMT, power supplies, and batteries.
- Reads the Trusted Platform Module PCR registers, the public endorsement key, and the endorsement key serial number.
- Reads the drive information (note: removable drives are not scanned).
Read file command READFILE
This command reads the DPD file specified by the –in option. The platform component information in the DPD file is directed to the console.
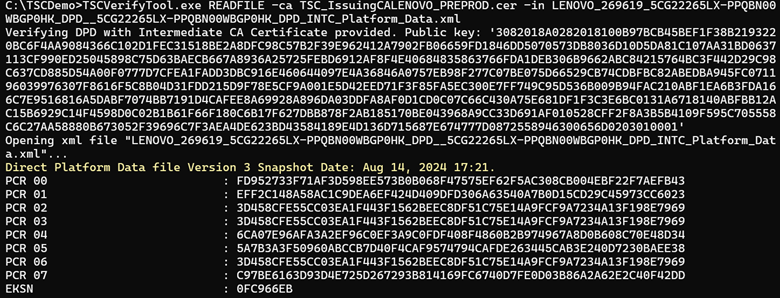
The DPD file is a signed XML file. Once the DPD file has been read, the XML signature of the XML file is verified against the TSC_Issuing CA. If the DPD file XML signature does not match, the following error message is displayed:
Direct Platform Data file: DPD_Filename.xml - XML file signature does not match.
Scan system read file compare SCANREADCOMP
This command scans the platform components and reads the DPD file specified by the –in option. The component change information is directed to the console. If the -fl option is used, the Platform Component Change data file is generated with the provided filename; otherwise, a default filename is used. This data file contains a consolidated summary of the results for the compare command.

After the compare operation has been completed the two success messages are displayed. The first one indicates tha the PCR information matched against the system. The second message indicates that all the components information matched against the systems.
If the results of the compare operation do not match, the following message is displayed:
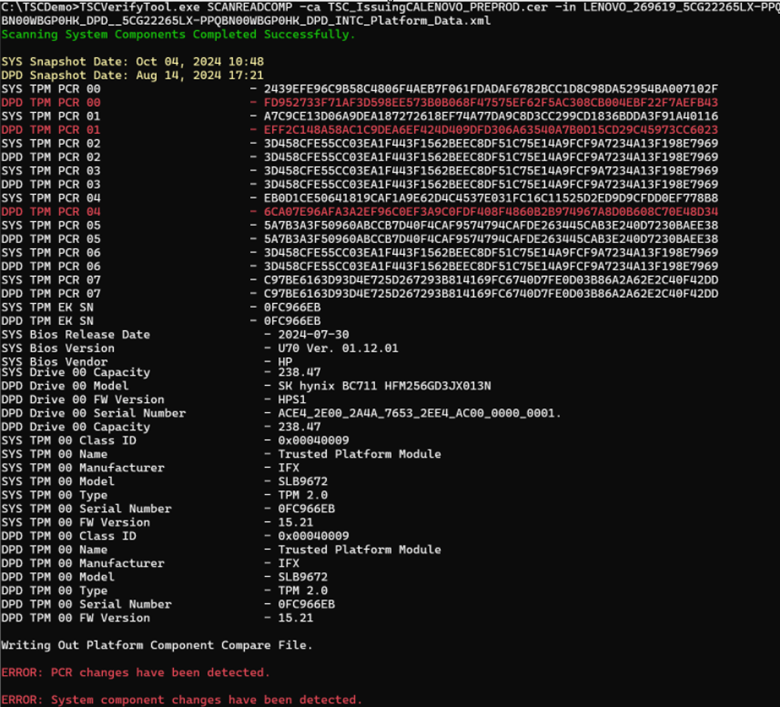
The changes between the System Snapshot data and the DPD are displayed line by line. Any Component Data changes are displayed in red.
It will display an error message if the changes were detected either on the TPM PCRs or at the system component level.
Platform component compare data file
After the comparison is performed, a Platform Component Compare data xml file is written. When the –fl option is used, it allows customization of the file name. If the –fl option is not used, the tool creates the file using a default filename.
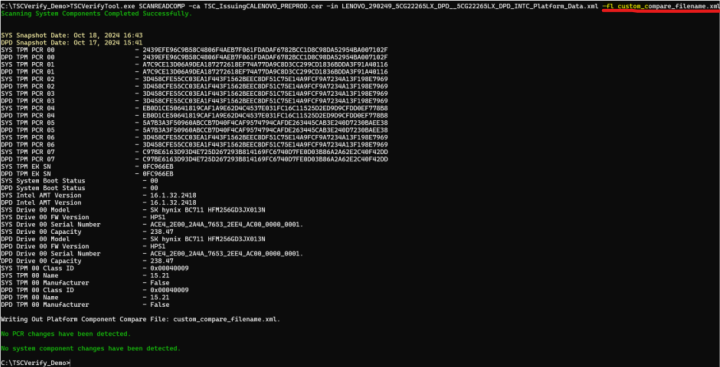
When the compare operation has been completed, the Platform Component Compare data file is created. If the results of the compare operation match, then the data file compare results will be true.
<?xml version="1.0" encoding="utf-8"?>
<PlatformComponentCompare ver="1">
<Header>
<SystemSN>PF0ZAQSW</SystemSN>
<Manufacturer>OEM_NAME</Manufacturer>
<Model>20L7002BUS</Model>
<DateTime>2020-08-13T11:21:38</DateTime>
<OEM>OEM_NAME</OEM>
<ODM>OEM_NAME</ODM>
</Header>
<CompareResults>
<CompareResult>true</CompareResult>
<ComponentScanCount>10</ComponentScanCount>
<ComponentChangeCount>0</ComponentChangeCount>
</CompareResults>
</PlatformComponentCompare>
Component changes

If the results of the Compare operation return changes, then the data file compare results are false along with the components that have changed.
<?xml version="1.0" encoding="utf-8"?>
<PlatformComponentCompare ver="1">
<Header>
<SystemSN>PF0ZAQSW</SystemSN>
<Manufacturer>LENOVO</Manufacturer>
<Model>20L7002BUS</Model>
<DateTime>2020-08-13T10:23:18</DateTime>
<OEM>LENOVO</OEM>
<ODM>LENOVO</ODM>
</Header>
<CompareResults>
<CompareResult>false</CompareResult>
<ComponentScanCount>10</ComponentScanCount>
<ComponentChangeCount>1</ComponentChangeCount>
</CompareResults>
<ComponentChanges>
<ComponentChange id="0">
<ComponentType>Bios</ComponentType>
<ComponentName>Default</ComponentName>
<SystemValue>2024-07-30</SystemValue>
<SnapshotValue>2024-01-18</SnapshotValue>
<ComponentName>Default</ComponentName>
<SystemValue>U70 Ver. 01.12.01</SystemValue>
<SnapshotValue>U70 Ver. 01.10.00</SnapshotValue>
</ComponentChange>
</ComponentChanges>
</PlatformComponentCompare>
Platform component compare data file XML schema
The Platform Component Compare data file XML schema is as follows:
<xs:schema attributeFormDefault="unqualified" elementFormDefault="qualified" xmlns:xs="http://www.w3.org/2001/XMLSchema">
<xs:element name="PlatformComponentCompare">
<xs:complexType>
<xs:sequence>
<xs:element name="Header" maxOccurs="1" minOccurs="0">
<xs:complexType>
<xs:sequence>
<xs:element type="xs:string" name="SystemSN"/>
<xs:element type="xs:string" name="GUID" maxOccurs="1" minOccurs="0"/>
<xs:element type="xs:string" name="Manufacturer"/>
<xs:element type="xs:string" name="Model"/>
<xs:element type="xs:dateTime" name="DateTime"/>
<xs:element type="xs:string" name="OEM"/>
<xs:element type="xs:string" name="ODM" maxOccurs="1" minOccurs="0"/>
<xs:element type="xs:string" name="MfgPubKeyHash" maxOccurs="1" minOccurs="0"/>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="CompareResults" maxOccurs="1" minOccurs="0">
<xs:complexType>
<xs:sequence>
<xs:element type="xs:boolean" name="CompareResult"/>
<xs:element type="xs:int" name="ComponentScanCount"/>
<xs:element type="xs:int" name="ComponentChangeCount"/>
</xs:sequence>
</xs:complexType>
</xs:element>
<xs:element name="ComponentChanges" minOccurs="0">
<xs:complexType>
<xs:sequence>
<xs:element name="ComponentChange" maxOccurs="unbounded" minOccurs="0">
<xs:complexType>
<xs:sequence>
<xs:element type="xs:string" name="ComponentType" maxOccurs="1" minOccurs="0"/>
<xs:element type="xs:string" name="ComponentName" maxOccurs="unbounded" minOccurs="0"/>
<xs:element type="xs:string" name="SystemValue" maxOccurs="unbounded" minOccurs="0"/>
<xs:element type="xs:string" name="SnapshotValue" maxOccurs="unbounded" minOccurs="0"/>
</xs:sequence>
<xs:attribute type="xs:short" name="id"/>
</xs:complexType>
</xs:element>
</xs:sequence>
</xs:complexType>
</xs:element>
</xs:sequence>
<xs:attribute type="xs:string" name="ver"/>
</xs:complexType>
</xs:element>
</xs:schema>
Platform certificate compare command PFORMCRTCOMP
This command compares the contents of the signed platform attribute certificate file specified by the –in option to the current system information. It detects changes in elements such as the EK Serial Number in the Trusted Platform Module and the Platform Serial Number in the system. It also compares the platform configuration from the file against the
current components from the system. The results of the comparison are output to the console.
The command indicates whether changes were detected at the system or component level as yellow warning messages.
If the result of the comparison is successful, a success message is displayed in yellow:
PFORMCRTCOMP PASS.
If the result of the comparison is successful, then it displays a failure message in red:
PFORMCRTCOMP FAIL.
The differences are shown line by line in red.
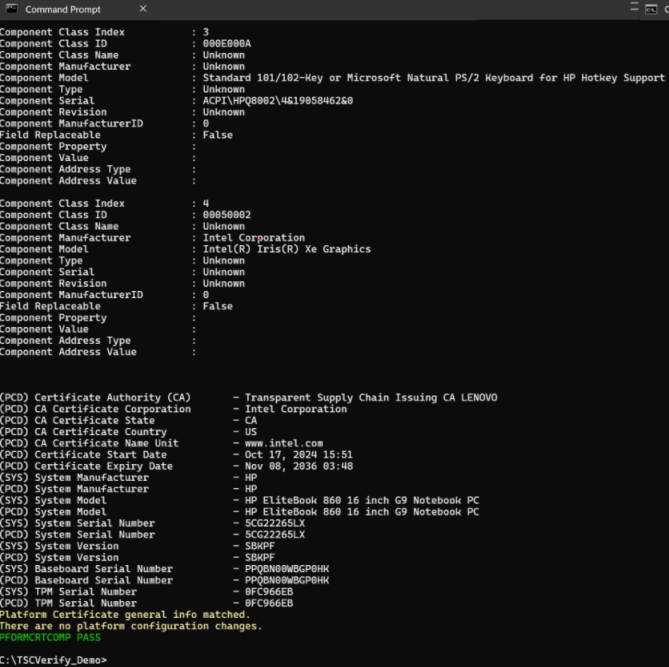
The Platform Certificate Verify function checks the Platform Certificate file issued for the platform against the platform itself, using the TPM as the hardware root of trust. It verifies that the system manufacturer, version, serial number, and motherboard serial number match the values in the signed platform certificate.

If the Platform Certificate matches the System values, the following messages are displayed:
Platform Certificate general info matched
There are no platform configuration changes messages
The Certificate Values are also displayed with a success message.
PFORMCRTCOMP PASS
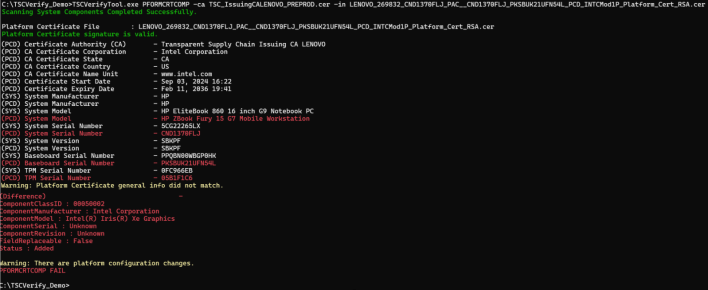
If the Platform Certificate does not match the System values, two messages are displayed in yellow:
Platform Certificate general info did not match - This message displays when the information that did not match is related to values like Serial Number, Model, Manufacturer, EK TPM Serial Number, and others.
There are platform configuration changes - This message displays when the differences found are related to platform components configuration.
All the differences are highlighted in red.
An error message is also displayed:
PFORMCRTCOMP FAIL
CA signature verify command CASIGVERIFY
This command verifies the signature of the TSC Issuing CA file. Optionally, it also enables verification of the signature of either a signed platform attribute certificate or a signed Direct Platform Data File using the public key of the TSC Issuing CA certificate. The TSC Issuing CA file is specified by the –ca file option. The signed platform attribute certificate or signed Direct Platform Data File can be specified by the –in option. The CASIGVERIFY command will only verify one file at a time.
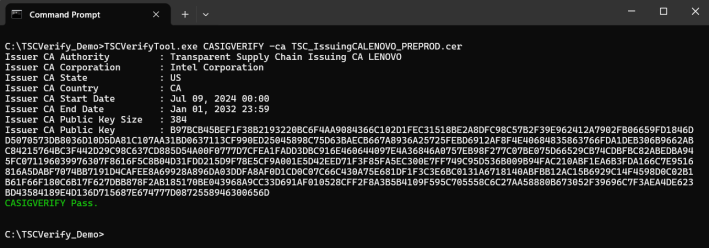
Passing signed direct platform data file
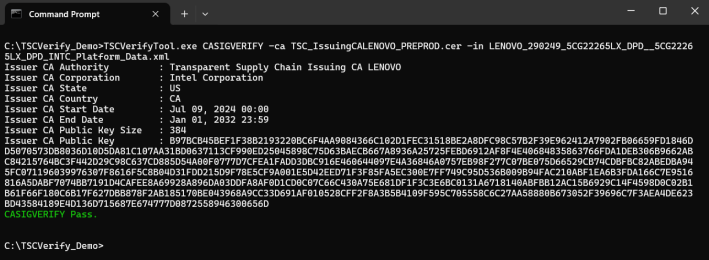
When no valid signed Direct Platform Data file is being passed, the command displays an error message.
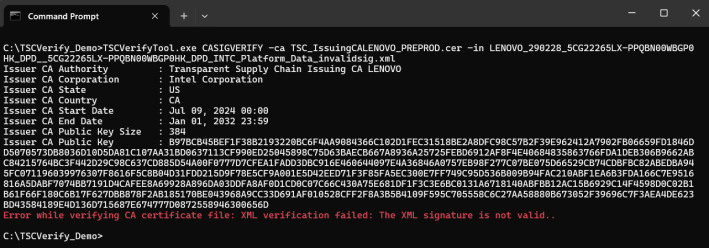
Passing signed platform attribute certificate
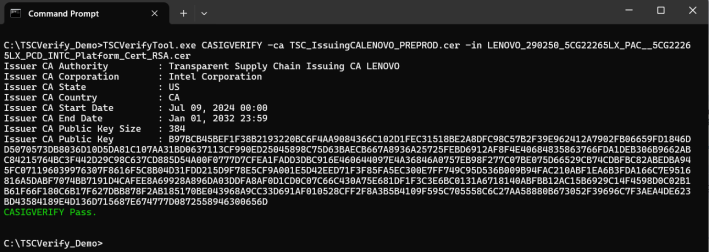
The Platform Attribute Certificate file and the Direct Platform Data file downloaded from the TSC Web Portal are signed using a PKI signing process. To validate the signature of these files, an Intermediate Certificate Authority file must be downloaded.
This Intermediate Certificate Authority file contains a public key that is used to verify the signature of the Platform Certificate file and the Direct Platform Data file.
Download this Intermediate Certificate Authority file and save it on the system. If you don’t know where to download your Issuing CA, please contact the TSC web portal team, and they will help you to retrieve your Issuing CA.cer file.
Write delta file command WRITEDELTAFILE
This command enables the generation of a new delta XML file that includes only the platform components that have been added, modified, or removed from the original system setup. It will perform a comparison of all the platform components based on current platform information by taking as input the base platform attribute certificate file and optionally passing a list of previous delta attribute certificate files.
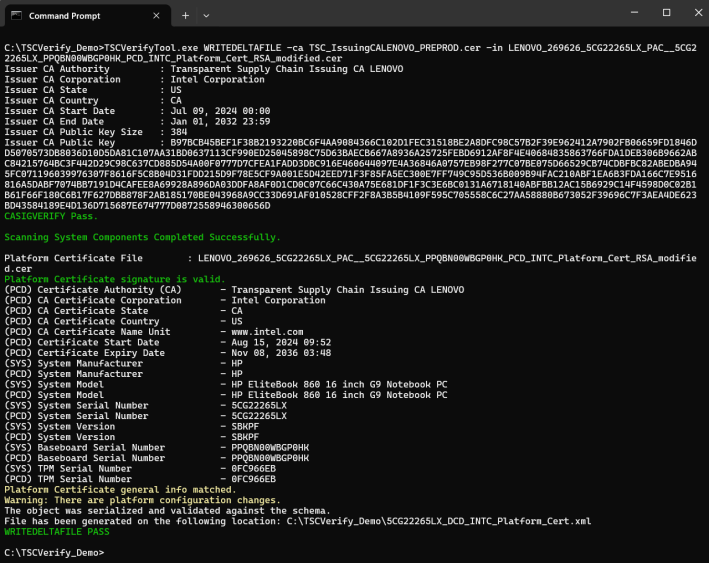
When you have a platform attribute certificate and one or multiple Delta certificates, you can generate a new Delta XML file containing the new system updates by adding to the previous command using the “-deltas” flag and the filename of the Delta certificate; if you have multiple Delta certificates, then you separate then by a space.
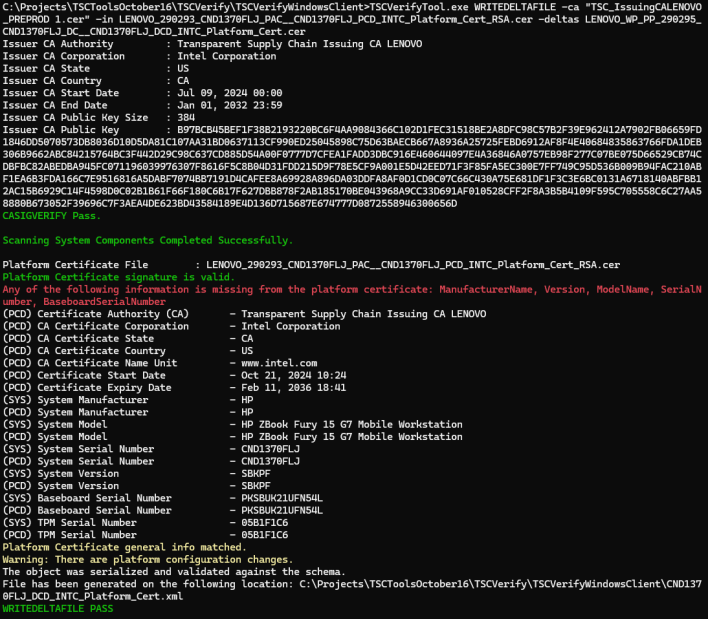
If no platform component changes are detected, the command will not generate the delta certificate data file and will display an error message.
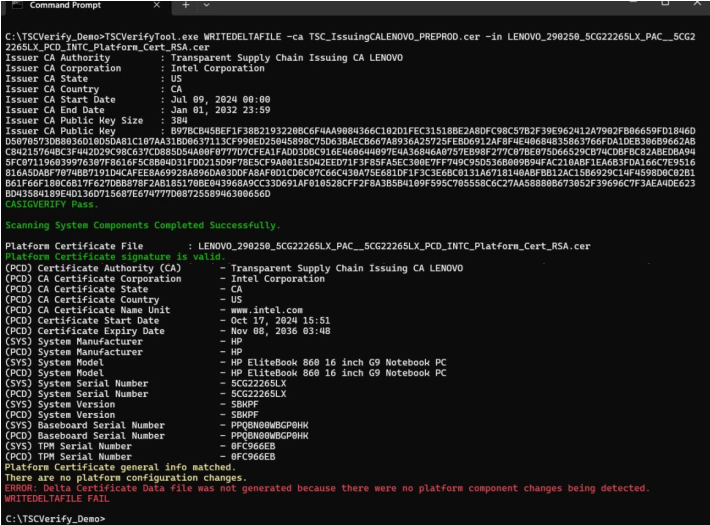
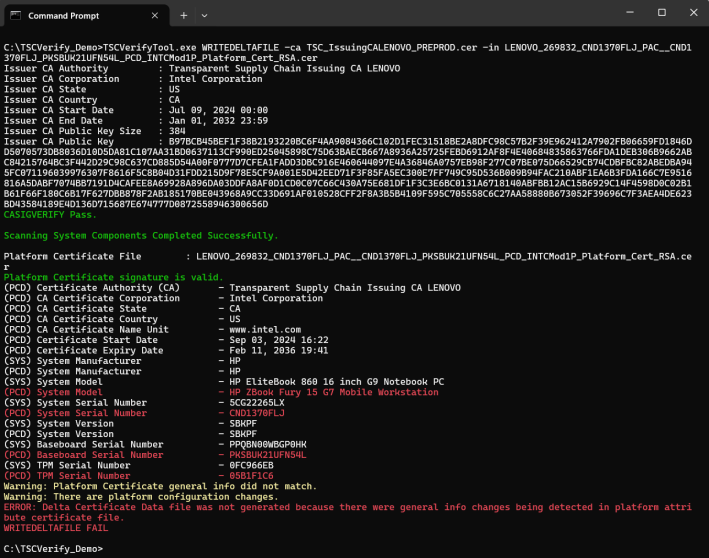
If a platform attribute certificate from another system is passed, the command will not generate the delta certificate data file and will display an error message.
Open-Source acknowledgments
This product includes software developed by the open-source community.
Bouncy Castle (Version 1.9) Bouncy Castle is a collection of APIs used in cryptography. It is licensed under the MIT License. Copyright (c) 2021 The Legion of the Bouncy Castle Inc. (https://www.bouncycastle.org) For more details, see the Bouncy Castle License: https://www.bouncycastle.org/licence.html
Microsoft TSS (Version 2.1.1) Microsoft TSS is a library for TPM 2.0. It is licensed under the MIT License. Copyright (c) 2019 Microsoft Corporation For more details, see the Microsoft TSS License: https://github.com/Microsoft/TSS.MSR/blob/main/LICENSE