Security Information and Event Management (SIEM) integration
This article shows how to integrate Intel® Trust Authority with 3rd party Security Information and Event Management (SIEM) services such as Splunk* or Datadog* to provide real-time notification of critical events such as attestation success or failure directly from your preferred reporting solution.
Note
Intel® Trust Authority SIEM events are approximately 12kb in size. Default Splunk* event sizes are limited to 10KB. Event messages larger than 10kb are truncated. Splunk* administrators can increase the Splunk* character limit to above 10,000 to prevent messages from being truncated.
- Successful attestation
The attestation token is sent to the SIEM platform upon successful attestation. Note that by default, this does not indicate that all policies were matched in the attestation. To enforce policy matching (and throw an error on policy mismatch instead of returning a token), the attestation request must set the optional
policy_must_matchvalue totrue. - Failed attestation If the attestation request returns an error response, the error will be sent to the SIEM platform. By default an error indicates a malformed API request or a failed attestation against the default policy. If policy enforcement is enabled in the attestation request, any policies that evaluate to unmatched will also throw an error and be included in the "failed attestation" event type.
The data pushed to SIEM is the same data recorded in the Reports and Metrics date-range reports. For more details about reports and metrics, see the Reports and Metrics article.
Note
By default, Intel® Trust Authority always provides an attestation token regardless of policy evaluation unless the attestation request forces policy compliance.
Intel® Trust Authority Configurations and SIEM integration
Only a tenant admin is authorized to manage, add, update and delete the system details of SIEM services.
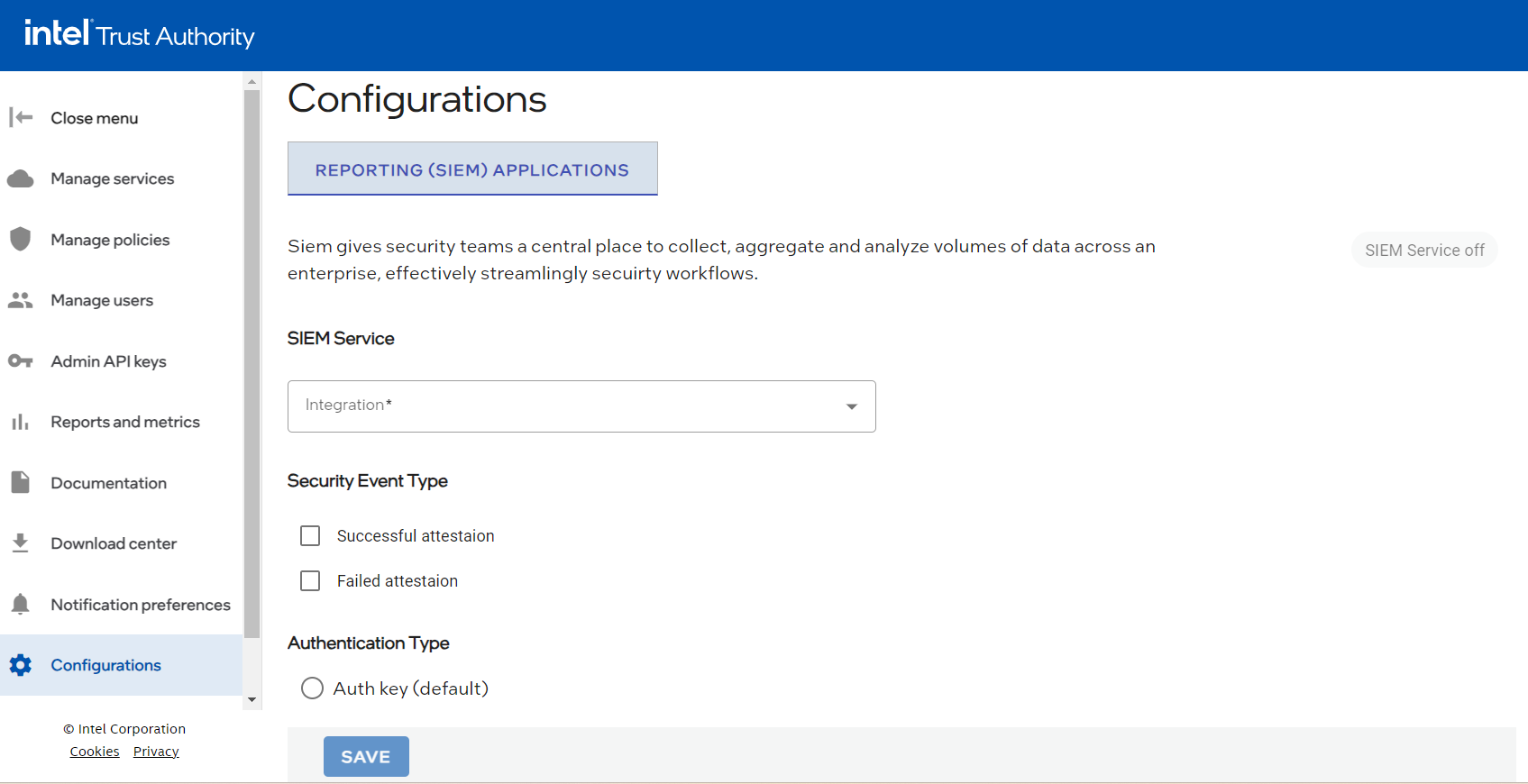
- The tenant admin logs into the Intel Trust Authority.
- Go to Configurations.
- Select Reporting (SIEM) applications.
Reporting (SIEM) applications
Complete the following sections to turn SIEM service on.
- Select a SIEM service.
- Select the type of security event(s).
- Choose the authentication type.
- Enter the endpoint URL and API key.
SIEM service
Select an available SIEM service from the drop-down list. In SIEM service (required), select one service from the list. - Datadog* - Splunk*
Security event type
Select option(s) for the security event type for real-time notification of critical events.
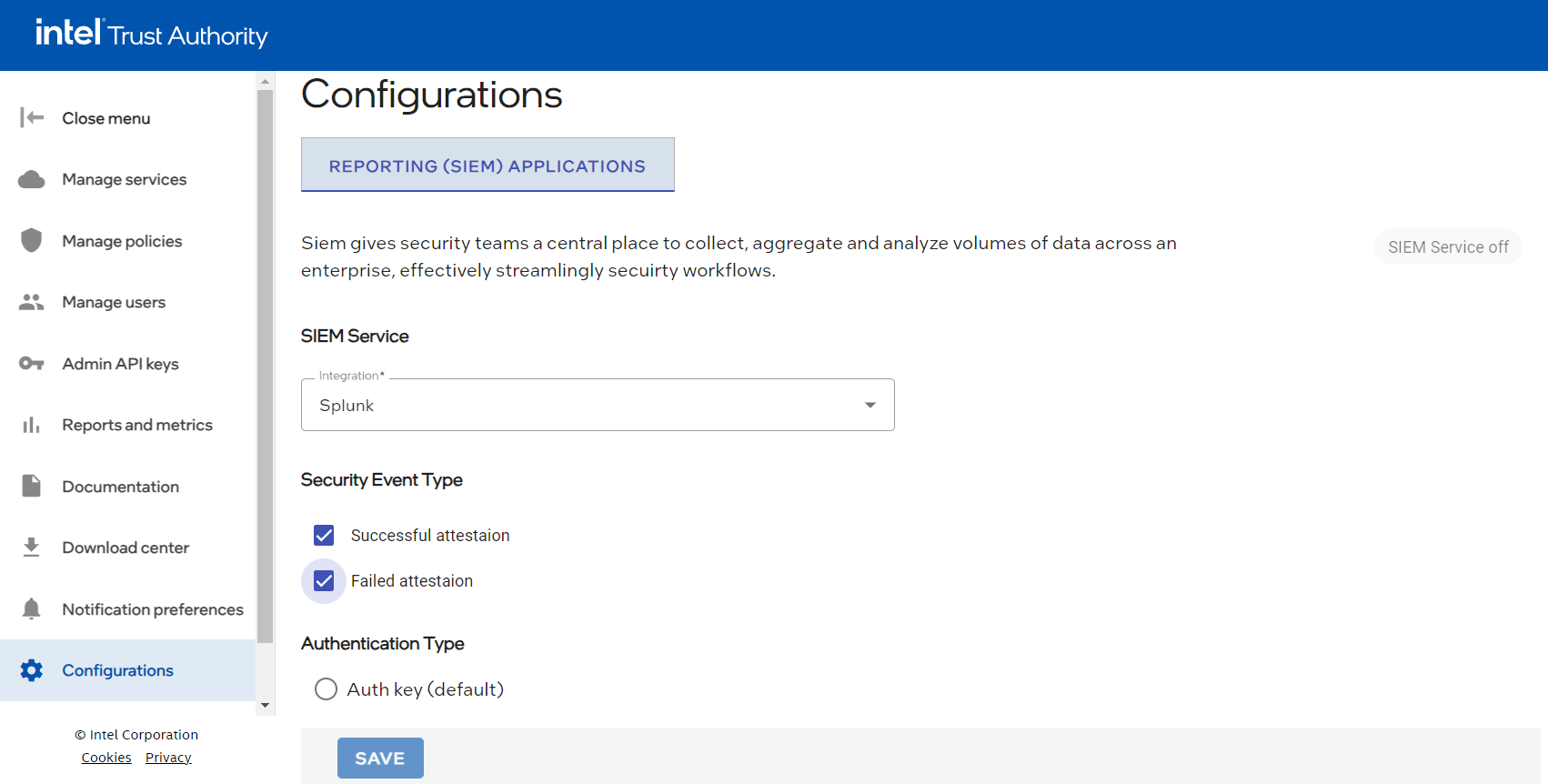
- Go to Security event type (required).
- Select from the checkbox options.
- Successful attestation
- Failed attestation
Authentication type
Select the authentication type.
- Go to Authentication Type.
- Select Auth key (default).
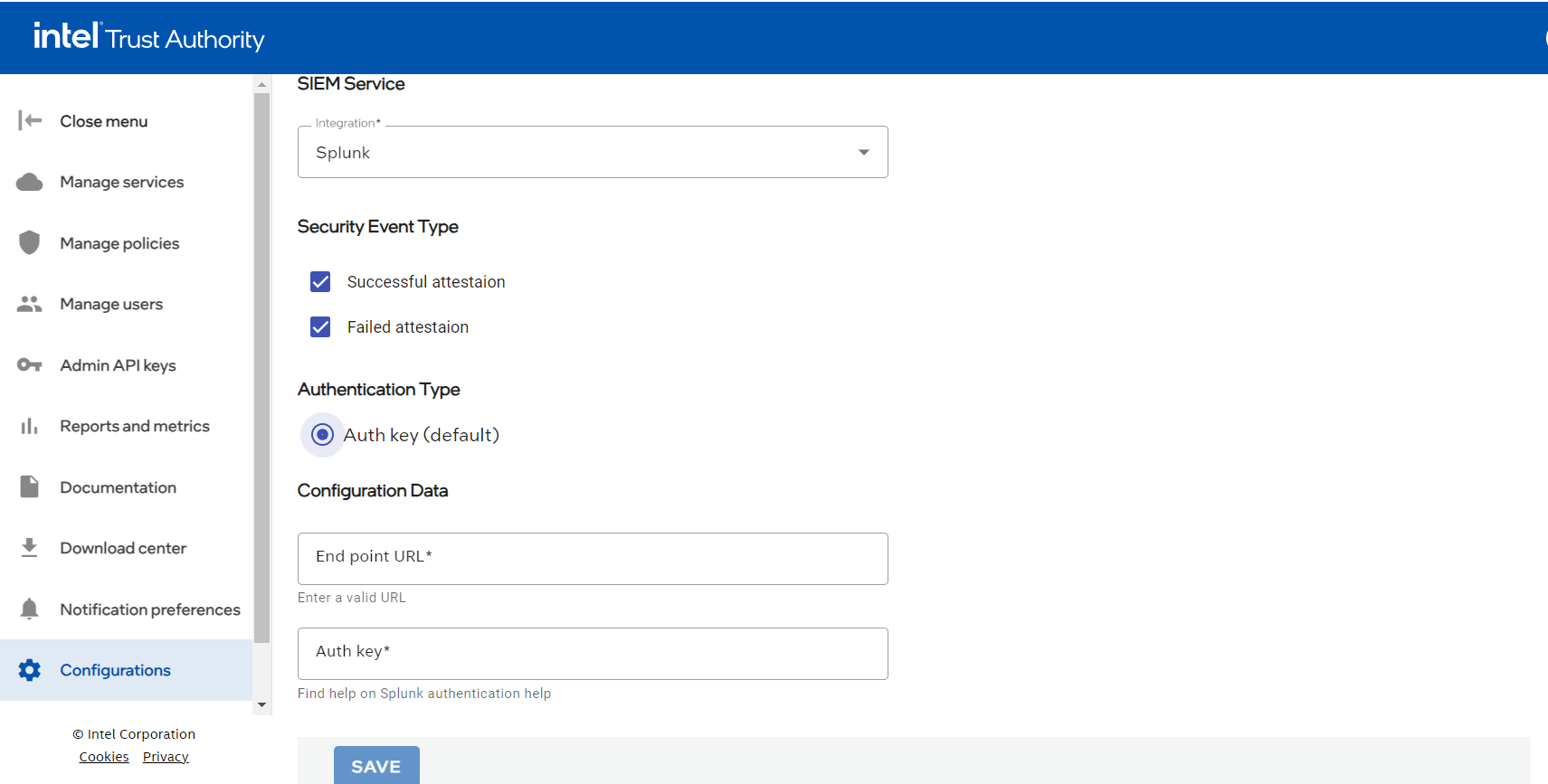
Configuration data
Enter the endpoint URL and API key. In Configuration Data there are two entry fields. Endpoint URL - enter a valid URL. Auth Key - enter the API key. A textual hint for user is provided that points to a location to find this data.
Save
Click the SAVE button. Upon successful validation, a green notification will display and the attestation token is sent to the SIEM platform
Upon failed validation, a red notification will display with information about the errors. Errors are sent to the SIEM platform.
* Other names and brands may be claimed as the property of others.